VMK Extraction from Bitlocker over SPI
Quick Links
Bitlocker VMK Extraction over SPI#
I’ve been doing some reading about Bitlocker and how it works recently and I had an occasion to reproduce some work done by others as an educational excercise.

Bitlocker in Theory#
Most operating systems allow you to use full disk encryption these days to encrypt your system storage drive. This is very handy, but there is a core design question regarding how the drive is decrypted. For Linux, you need to provide a password to boot the computer. If you loose the password, I guess tough.
Microsoft’s solution is to store the encryption keys inside a chip called a TPM, or Trusted Platform Module. Then, it only releases them if the TPM is happy with the boot situation. The bitlocker boot process provides information to the TPM about the software and hardware state at each stage of booting. Then, the TPM releases the encryption keys if any only if these parameters match the expected values.
Some modern CPUs have the TPM on-board the CPU die itself. However, it is still pretty common for it to be a separate chip.

Here is one such separate chip from a laptop motherboard.
Now, the thing about being a separate chip is that it needs to communicate with the CPU in order to divulge the encryption key.
In this case, the key is transferred using a low level bus called the serial peripheral interface.
SPI is not encrypted, but to witness this communication you’d need to know which pins on the TPM chip are being used to communicate, and often they are in a package (chip shape) that places the pins under the chip so it is difficult to connect to a logic analyzer or other tools.
However, it is also common for the TPM to be on the same SPI bus as another chip, a flash rom chip. This is demonstrated neatly by the schematic of the framework 13 11th gen:

So, instead of listening in to the TPM traffic itself, we can listen in to the flash rom chip.
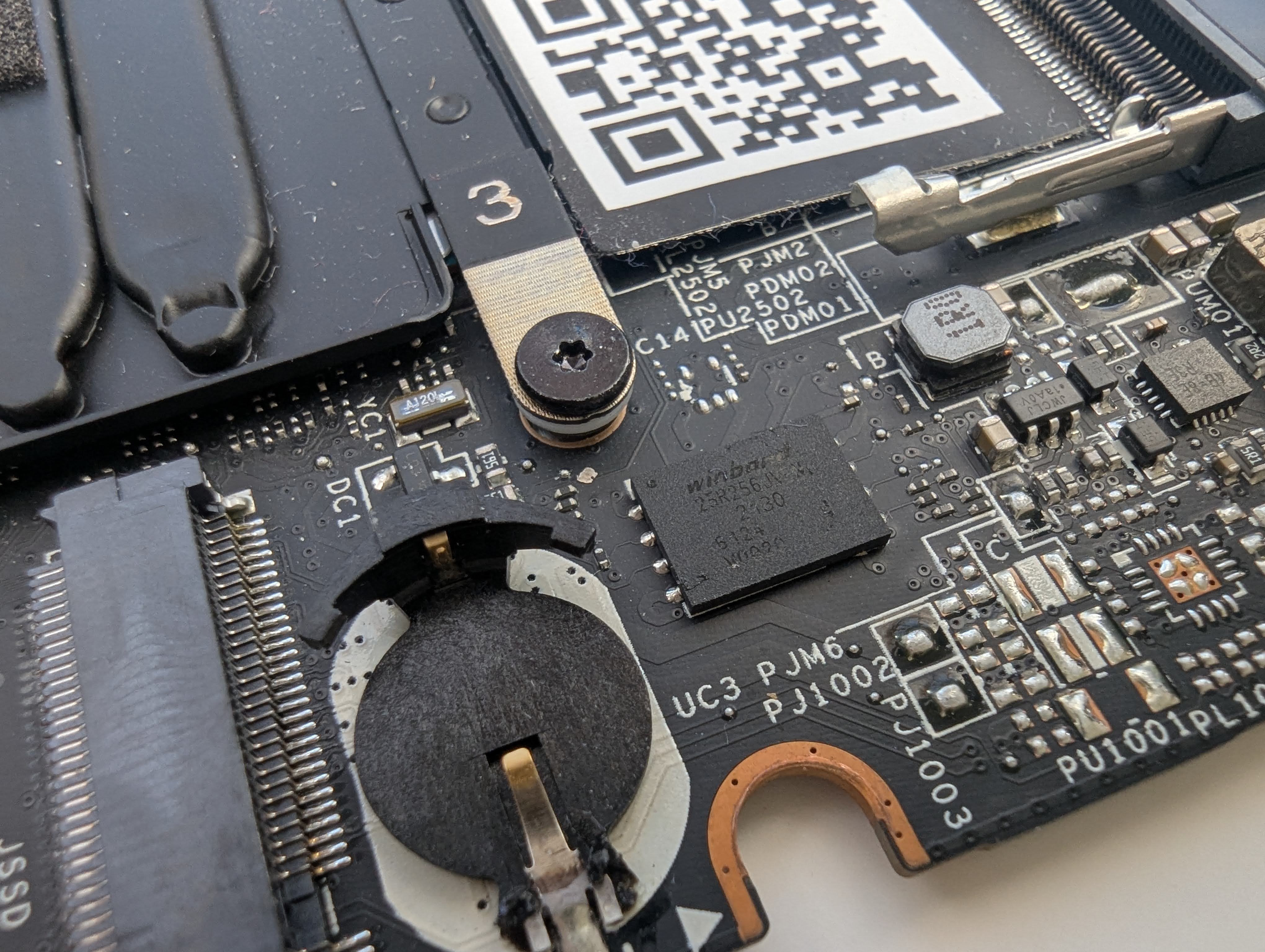
On this example laptop, and in several of the other motherboards others have tried, it also seems like this chip is often easier to access as well which helps a lot for the next step.
So, all we need to do is use a logic analyzer and listen to the signals while the laptop boots, and we should observe the key.
Practice#
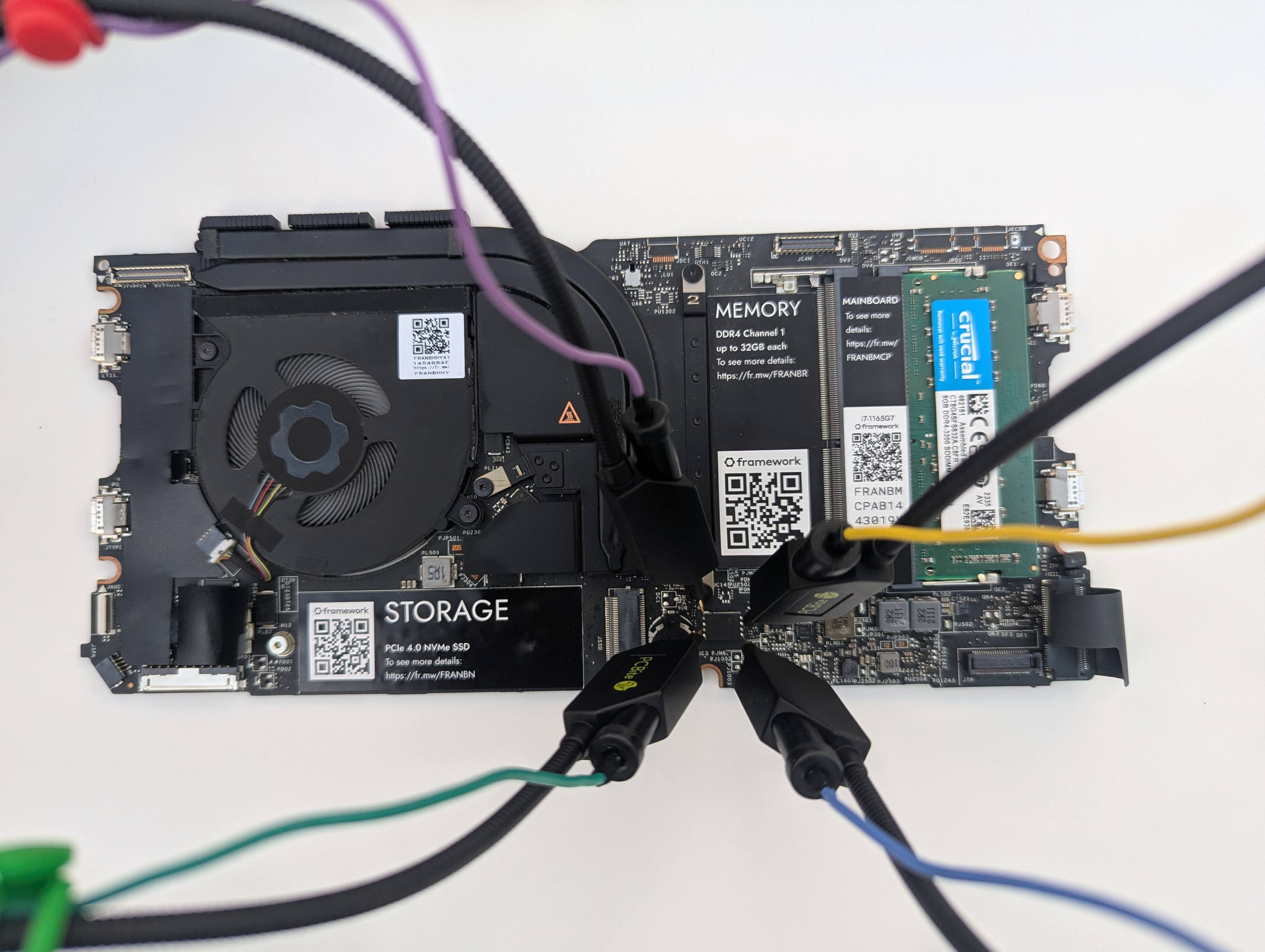
Now both flash roms and TPM chips, as far as I have read, are capable of using a version of SPI called Quad SPI, wherein 4 channels are used to communicate. To analyze this we would need those 4 channels, plus a clock channel. However, from what I can tell right now it seems like it is more common for TPMs to communicate the encryption keys using single SPI. Which makes it easier for us because we can connect fewer probes, just 3 are enough.
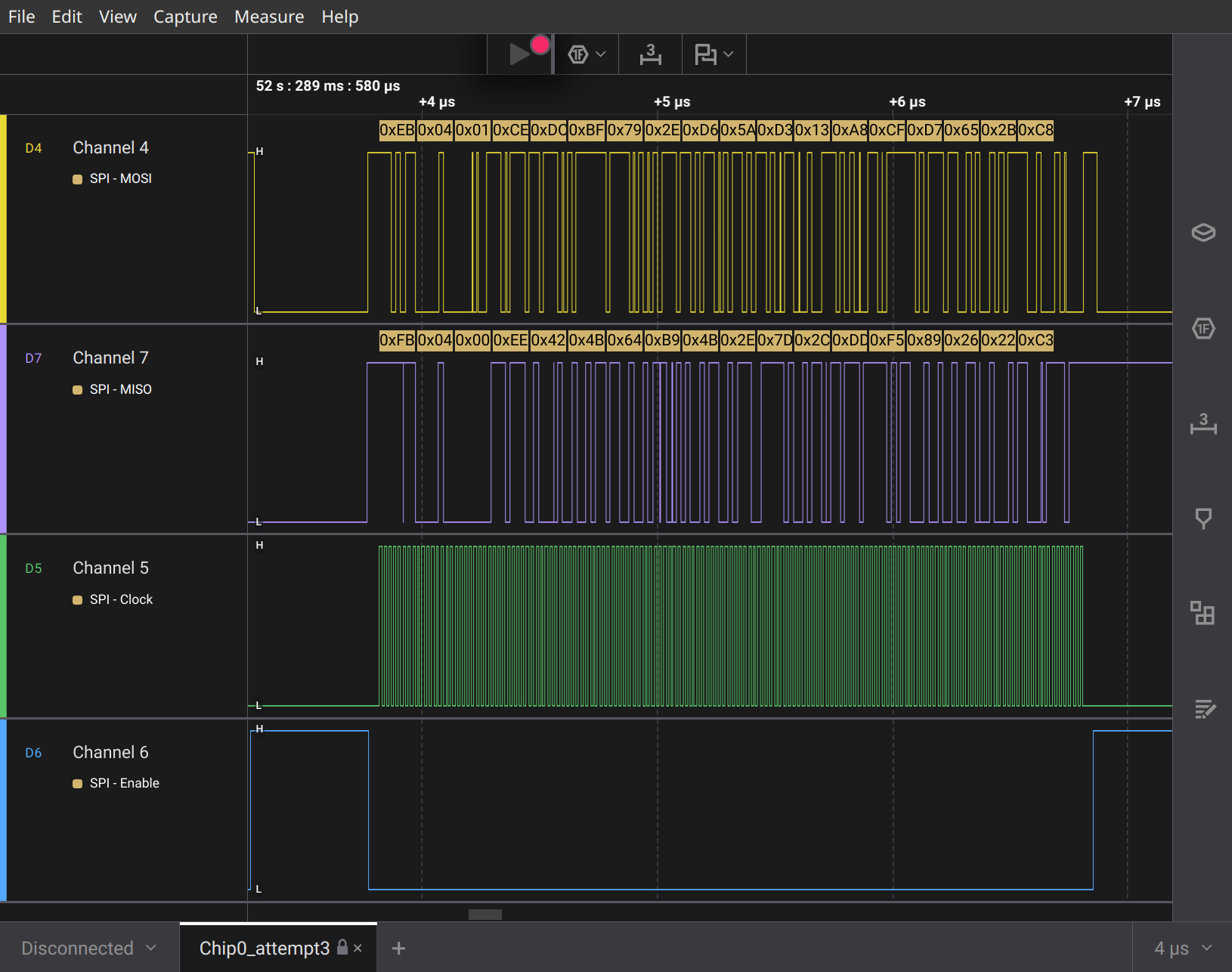
Now this logic analyzer has built-in support for SPI, however I never managed to find the actual key using this raw data. Instead, there is an extension that parses the SPI transactions according to the bitlocker spec.
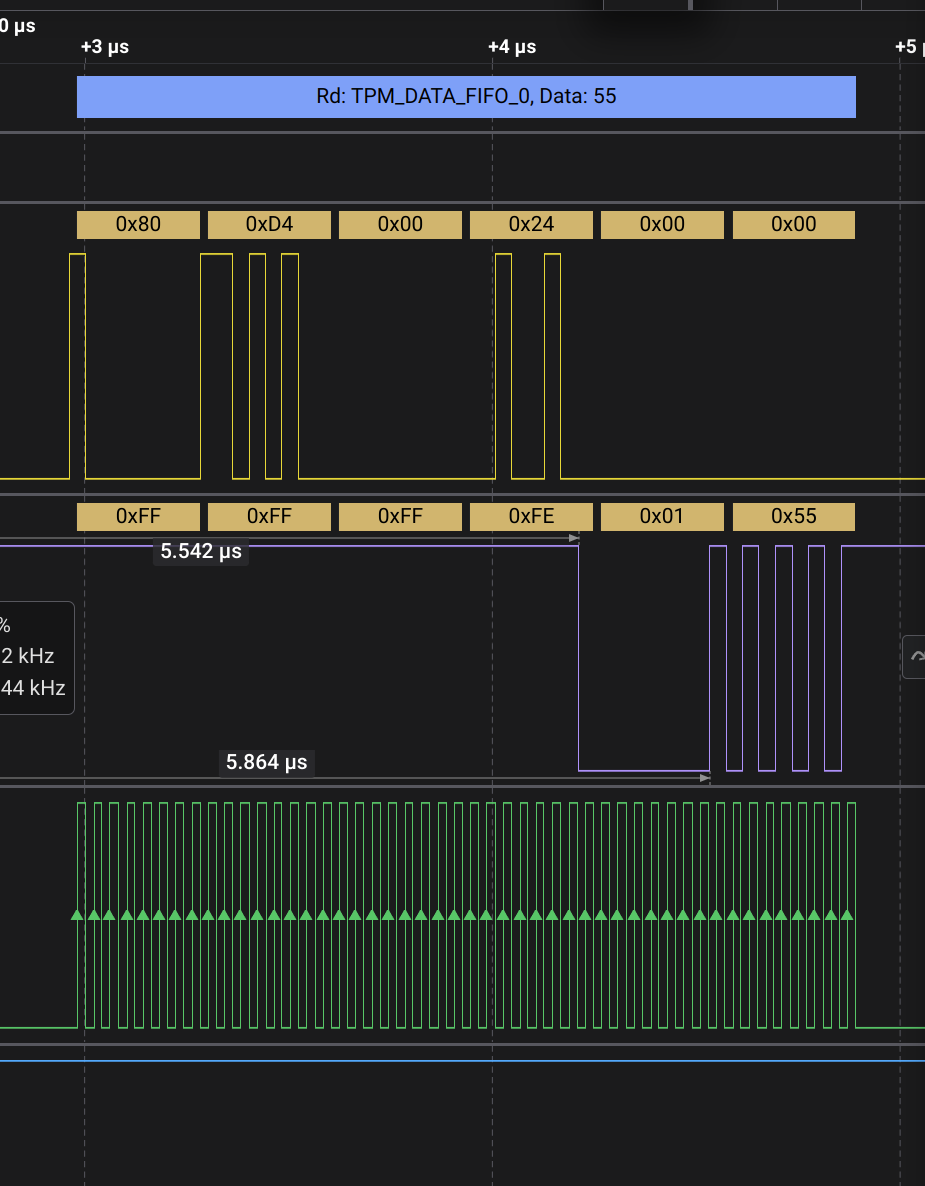 This extension is bundled with a “high level analyzer” that also skims through these transcations and grabs the one containing the encryption key.
This extension is bundled with a “high level analyzer” that also skims through these transcations and grabs the one containing the encryption key.
References#
Bitlocker toolkit for Saleae Logic
The original blog where I read about bitlocker key extraction
Framework Motherboard schematics
https://post-cyberlabs.github.io/Offensive-security-publications/posts/2024_09_tpmandpin/
https://pentests.nl/pentest-blog/tpm%E2%80%91sniffing-with-saleae-logic-analyzer/